Vulnerability Assessment and Penetration Testing

Vulnerability Assessment (VA):
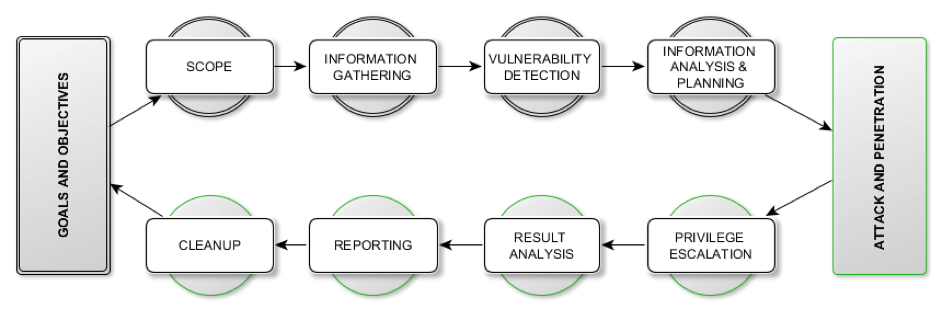
The first step of the VAPT process involves performing a vulnerability assessment of your assets using our state of the art automated tools combined with manual testing techniques to identify all breach points & loopholes and to determine the security posture of the target systems. By identifying all the breach points/loopholes, we are able to put in measures to block a potential attacker from exploiting them thereby safeguarding against hacking/exploitation.
Penetration Testing (PT):
The second step in the VAPT process involves performing a penetration testing. During this step, our penetration testers will simulate the activities of a malicious attacker who tries to exploit the vulnerabilities identified in the first step (VA) as an input vector.
As part of the overall VAPT process, CyberHawk provides a comprehensive report on the effectiveness of the security measures that are present in your network and recommend a set of measures that need to be put in place to ensure that identified vulnerabilities are dealt with accordingly, offering our expertise in resolving all identified vulnerabilities.

- The Volta Place, 35 Patrice Lumumba Rd Airport Residential Area
- info@cyber-hawk.com
- (+233) 0593961550
- www.cyber-hawk.com